Asymmetric cryptography and hashing functions are a complex topic for ordinary users. However, anyone who wants to use a cryptocurrency wallet safely should know the basics. We will not discuss how exactly and why cryptography works. We will explain the basic principles of cryptography from the perspective of wallet users. We tell you how cryptographic tools are usually used. There will be some theory in the article, but we promise, no math. We will try to find analogies that facilitate understanding. The article does not aim to be comprehensive and terminologically accurate.
If you want to keep your ADA coins safe, you need to learn basics. As you will see, you don’t have to remember that much. If you don’t want to deal with theory, look at least at the last section dedicated to wallets.
I have heard something about a key
Cryptography is the practice and bunch of techniques for secure communication in the presence of third parties called adversaries. Cryptography is about constructing protocols that prevent third parties or the public from reading private messages and data. It also deals with various aspects of information security, data confidentiality, data integrity, authentication, and non-repudiation.
Most users probably use cryptography for converting ordinary readable plain text into unintelligible, unreadable text (just a “mess of characters”, also called ciphertext) and vice-versa. Imagine that you have some text and you don’t want someone else to read it. It’s your secret you want to protect. At the same time, you want to be able to easily access the original form, or send the secret over the Internet to someone else and allow him to read the document.
Once the original text is converted into an unreadable form, nobody is able to deduce the original form. The content of the document is thus safely protected from misuse.
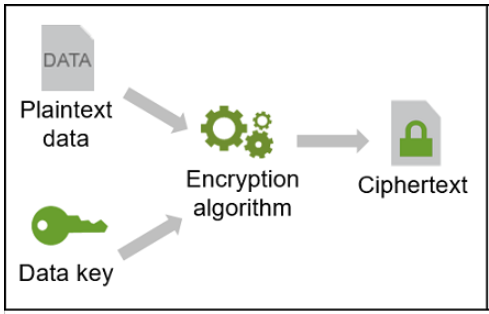
The conversion process, when a readable form of a document is converted into the unreadable form, is called encryption.
The opposite process of making illegible forms readable again (the original form is recovered) is called decryption.
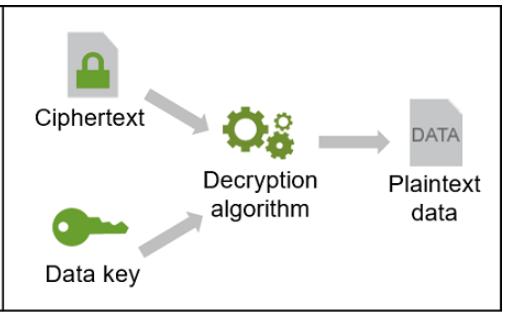
Let’s say that I have some secret written in a document (just a file). Cryptography allows me to convert the document into an unreadable format (encryption) so I can have it on my computer or send it via the internet to somebody else. The point is that nobody else is able to read it. If I want to let somebody else read the document I have to provide him with the secret. Only I know the way how to convert unreadable form back into a readable document. It means, restores back the original form of the document.
The conversion process (encryption) needs three things:
- A cryptographic algorithm, what is basically a function that takes some parameters as an input to produce output. The algorithm is based on complex mathematics and you can imagine it as a set of rules that dictate what to do to convert the original text into an unreadable form.
- A digital input that is to be converted into an unreadable format. It can be a file or plain text. It is what should be protected.
- A cryptographic key. The cryptographic key is a piece of information that determines the output of the cryptographic algorithm. In addition, the key is used for the reverse process and makes it possible to restore the original form. Without the key, there would be no chance to restore the original form after encryption.
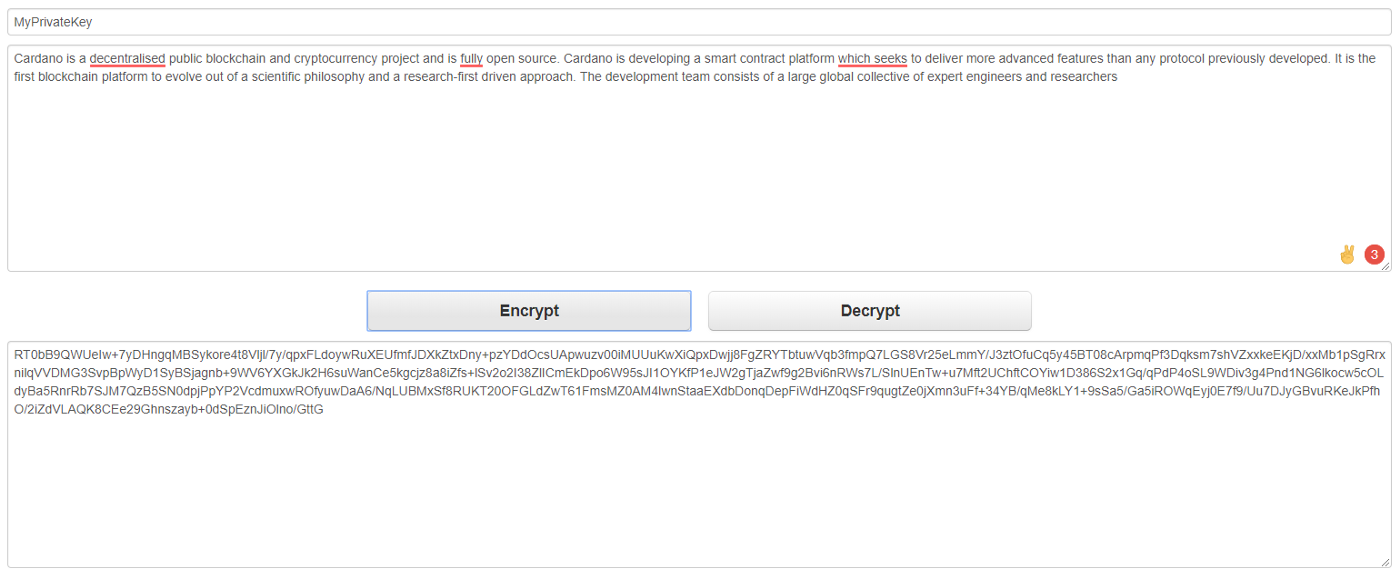
Notice, that the cryptographic key and file are inputs for the cryptographic algorithm. The algorithm behaves always the same. Different inputs for the algorithm results in different outputs. If you choose to encrypt one file multiple times and use a different key each time, you will receive different encrypted texts (ciphertext). For example, you can use key A and key B to produce ciphertext A and ciphertext B. Both ciphertexts are significantly different despite the input file was the same. Used key made the difference. To decrypt ciphertext A only key A must be used. Notice that using key B to decrypt ciphertext A will not produce readable text.
Once the cryptographic algorithm produces a result ciphertext you can delete original data in the plain text including all copies. You are able to get the original file again from the ciphertext via using the key. So you have to keep the key in a safe place!
Is it complex? Think of the encryption process as a meat grinder. When you put the beef meat and a bit of salt into the meat grinder, the mash comes out. Eating the mash you have no chance to recognize that beef meat was used as an input. When you put the pork meat a bit of salt, the mash comes out again, but a different one. However, the taste of the mash will be very similar to the previous one.
The inserted meat and salt determines the quality of the mash. The meat grinder represents the cryptographic algorithm. The meat is a readable input (text) and salt is a cryptographic key. The mash is the unreadable output. Every piece of meat and salt is unique so the output mash is unique as well.






